Advancements in web and BYOD technology have led to more convenience for employees who want to conduct financial transactions or make purchases online. At the same time, identity thefts have increased in number as cyber criminals continue to infiltrate networks and systems in an attempt to steal passwords.
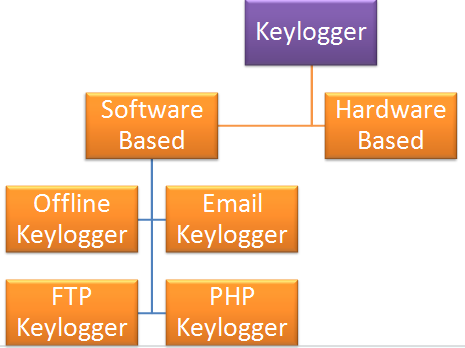
One of the most interesting (and dangerous) techniques used by hackers to breach passwords is ‘keystroke logging’. A small malicious program called a ‘keylogger’ gets installed on an employee’s computer before cyber criminals can record keystrokes.
Employees may accidently install a keylogging application in the following ways:
Add-ons: Allowing add-ons to be downloaded from malicious sites. Executable files may contain a keylogger virus, so before downloading a file, it is important to ensure that it is being downloaded from a trusted source.
URLs: Opening an untrustworthy URL. Some web pages may have code in them to exploit a web browser and cause to install a keystroke application without the user’s permission. Sometimes hackers may serve a legit page or two from an official site before the user is redirected to a malicious web page.
Software: Legitimate software may include a keylogger function which can be used to see program functions with hotkeys. Most of such software is created for administrators, who want to track what employees do throughout the day. However, this software can also be used by adversaries to steal confidential information like passwords.
Typically, keyloggers don’t cause any damage to the infected system like other malicious programs do, which makes it more difficult to detect if the system was infected. The virus can monitor:
- Documents accessed and websites visited, with screenshots of browsing activity
- Video and voice recordings from device camera and microphone. However, these features are often disabled because recordings take a lot of space and are difficult to send to a remote server un-detected.
- Everything typed on the keyboard, including passwords, private chats, emails, and items that are copy pasted.
This all sounds concerning, but the good news is there are ways to protect yourself and your employees from keylogging programs. Here’s a run-down of what you can do to protect your passwords:
1. Firewall
A keylogger in most instances transmits the collected information to a third party to inflict harm, which involves sending out information via the web. While close monitoring of network usage may lead to detection, the bandwidth taken up by keystrokes is almost undetectable, so you can’t count on monitoring as a means of detection.
A firewall would be a better option as it closely monitors your device’s activity. It will display a warning or seek your permission when a program attempts to send out data. Modern firewall offerings also have the option of disabling the transfer of outbound data completely.
2. Password managing software
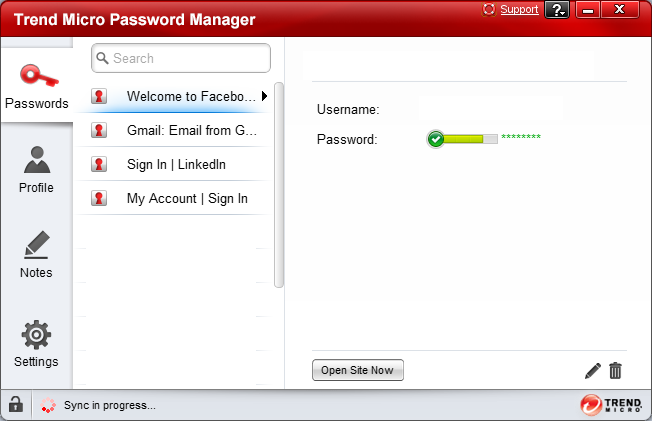
Keyloggers gather raw information before shipping it out to a third party. However, they can’t keylog what isn’t typed, nor can they function where a password is encrypted. As a result, a password manager that includes keystroke encryption and one-click login to all accounts can protect your passwords from being read by cybercriminals. Also, employees and administrators can use such a software to change weak passwords, to reduce chances of hijacking. Trend Micro lists password management software as a crucial element of internet security, as weak passwords can minimize the damage in case a hacking attempt is successful.
3. Keep software and apps up-to-date
Keyloggers, like most malware programs, can exploit app and software vulnerabilities to inject themselves into a device without the user’s permission. Outdated software and apps can make it easy for malicious sites to download the keylogger on your system.
So it’s important to make sure all your running apps and software are updated to the latest version released by their vendors. While updating software can be inconvenient, it’s a proactive strategy to stop attacks when it matters the most.



More Stories
How to Effectively Remove ChocoEukor from Your Android Device
From Pixels to Perfection: Mastering the Art of Web Design
How to Stop TinyTask: 10 Effective Techniques for Gamers and Tech Enthusiasts